Enterprise-Grade DDoS Protection
with Advanced Firewall Management
Secure your infrastructure with our powerful DDoS mitigation. Our Shield Panel provides real-time attack monitoring, intelligent traffic filtering, and advanced edge-level protection to keep your services online during volumetric DDoS attacks.
Automated Protection
Real-time attack mitigation
In Depth Analytics
See what's going onPowerful Tools
Filter traffic accuratelyEnterprise DDoS Protection
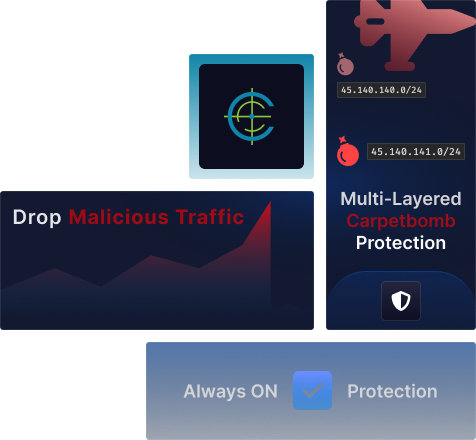
Protect your infrastructure with our enterprise-grade DDoS mitigation. Our advanced protection system combines real-time traffic analysis, intelligent filtering, and automated threat response to ensure your services stay online during attacks. Built for businesses that require always-on protection against evolving DDoS threats.
Intelligent Traffic Analysis
Advanced behavioral analysis automatically distinguishes between legitimate users and attack traffic. Our intelligent filtering ensures business continuity while effectively blocking DDoS attacks of any scale.
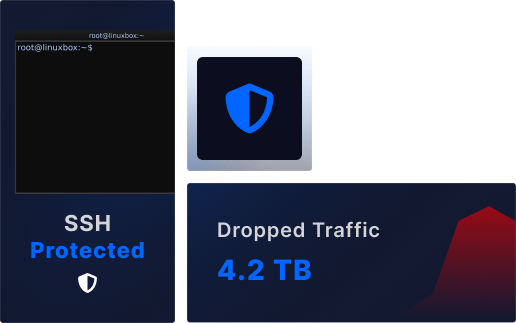
Real-Time Attack Mitigation
Instantly respond to threats with our Shield panel's automated defense system. Configure custom protection rules and leverage our intuitive dashboard to maintain complete control over your security posture.
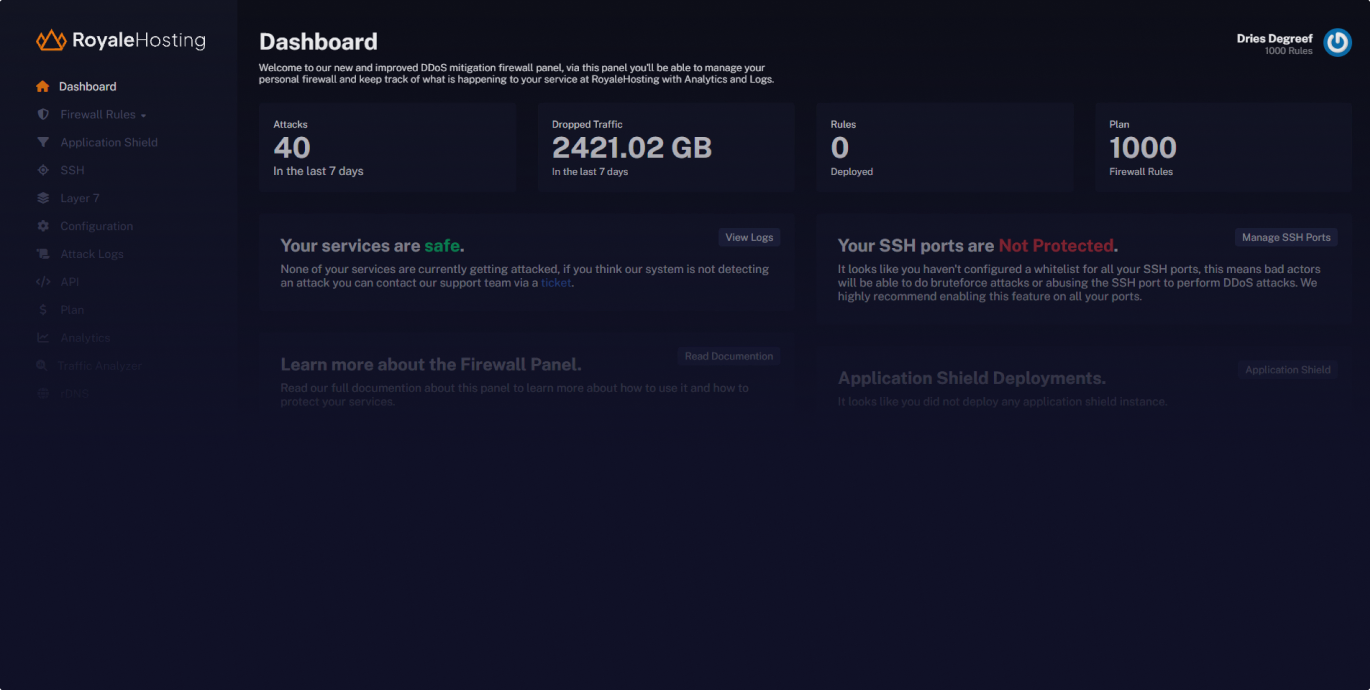
Advanced Security Analytics
Monitor attack patterns and protection effectiveness with comprehensive security analytics. Get detailed insights into traffic behavior, attack vectors, and mitigation performance through our advanced reporting system.
Note: Protection at our New York location is limited and not all shield features are available.
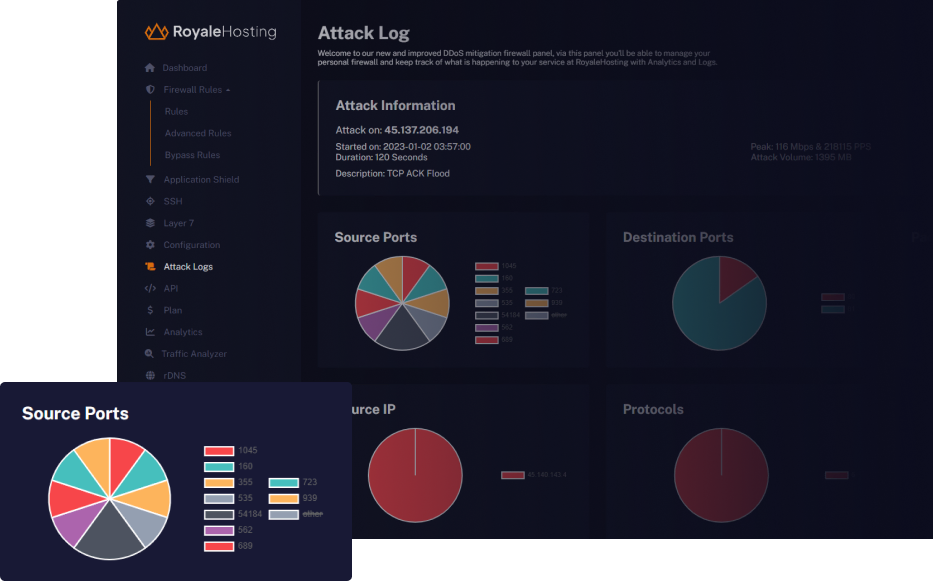
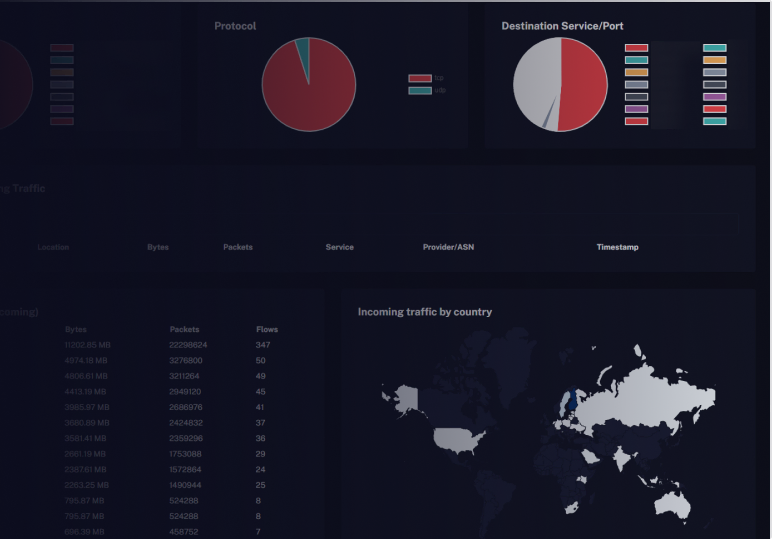
Attack Insights
Our Shield Panel provides real-time insights into the filtered traffic during attacks. With a range of available metrics, you can monitor and analyze the impact of attacks on your service.
- Source Port
- Destination Port
- Packet Length
- Protocols
- ASN
- Country
Analyze traffic
With our powerful tools, you can analyze and understand the traffic directed towards your server. Gain valuable insights into the patterns of incoming attacks, enabling you to make data-driven decisions to optimize your server's security.
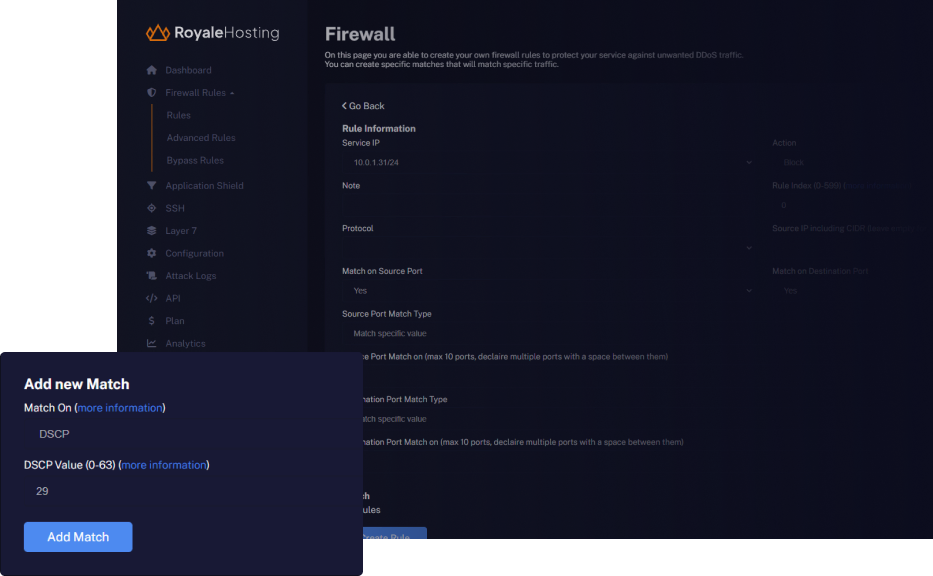
Deploy rules
Deploy rules on our edge with ease to strengthen your protection measures. Our platform offers a seamless experience for configuring and implementing rules that safeguard your service from potential threats.
- Protocol
- Source Port
- Destination Port
- TCP Types (SYN, ACK, FIN, RST, etc...)
- Fragments
- Packet Length
- ...
Under Attack? Contact us.
Need help dealing with DDoS Attacks? Contact our experts for immediate support and effective DDoS protection strategies.
Contact us ->